Observing Live Network Traffic with Wireshark
Wireshark + tcpdump + ssh = inspect network traffic live
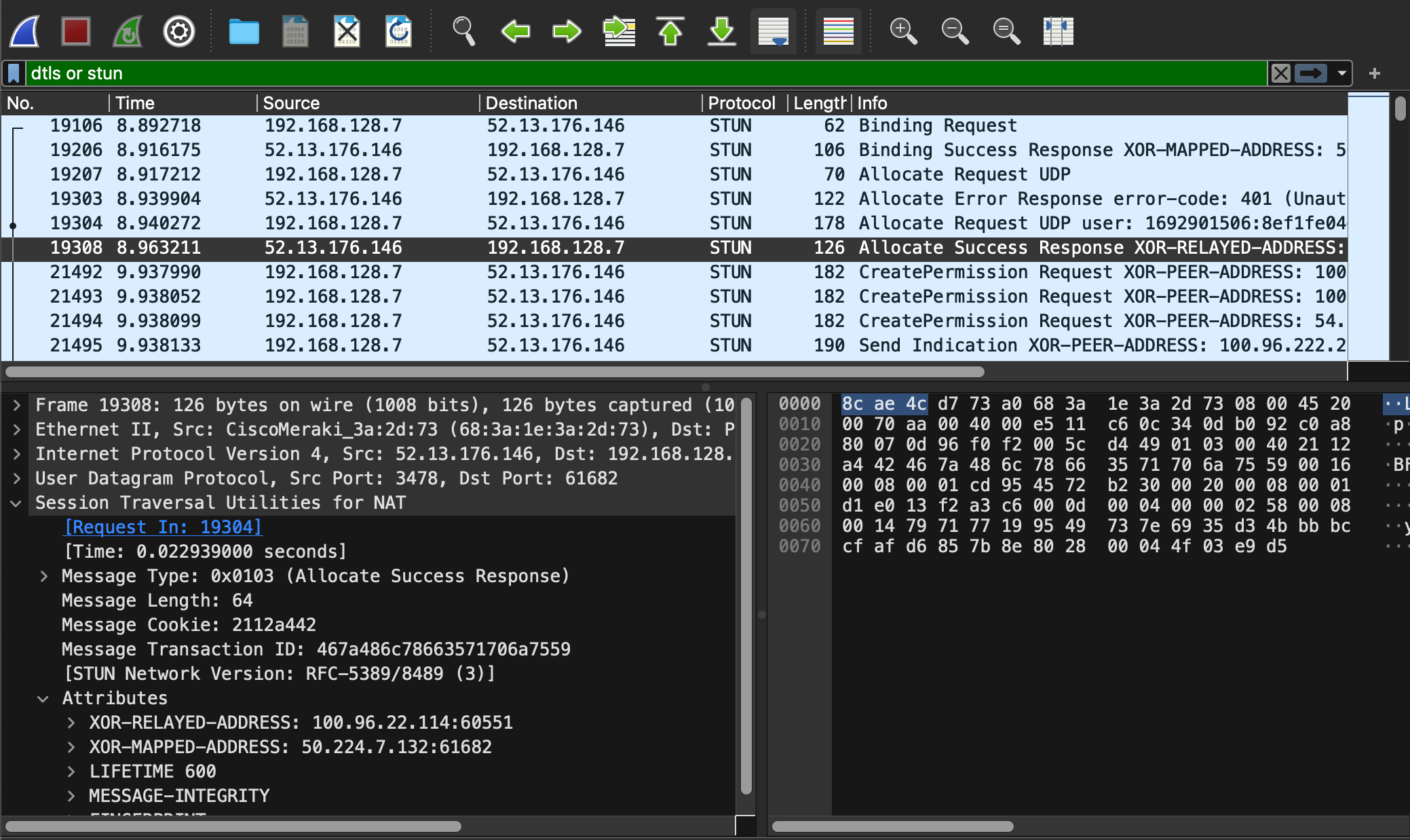
If you have to work with network packets, it is often useful to see actual traffic that you can analyze later. Wireshark is one of the most helpful tools for this. It can load PCAP captures, parse, and annotate the individual packets so you can see what's going on. Capturing traffic is easy with tcpdump utility. However, if what you are capturing happens over long durations, or requiring some other external triggers, generating that capture file isn't so easy. But if your target runs Linux, then there is a way.
Software You Need
- You need
tcpdumputility, which you can download source from this web site. On that same site you also need libpcap, the library that does the actual work. To build your owntcpdump, first build libpcap. You should also consider building static libpcap.a so that yourtcpdumpis a single binary without the need to find libpcap.so at runtime. - You need a SSH daemon like Dropbear. This allows you to execute commands on remote target.
- Wireshark. Your favorite Linux distribution probably already has a version, this helpful software is cross-platform.
Setup
Make sure you can SSH into your target, and that tcpdump command is in your path; test connect to your target at least once so you can add its public key. Then, from your local terminal:
ssh -oHostKeyAlgorithms=+ssh-rsaroot@<IP address> '/tmp/tcpdump -U -s0 -w - "not port 22"'| wireshark -k -Y "<filter>" -i -
Replace <IP address> with your target's IP and <filter> with Wireshark display filter, that's it!
You can look up the meaning of the switches easily, but to quickly break them down:
-oHostKeyAlgorithmsis only necessary if remote server is complaining about which cipher suite you are using. OpenSSL server will automatically drop connection if client doesn't report that it understands the key used to sign X509 used during handshake, for example."not port 22", because we are transferringtcpdumpoutput over SSH, you don't want to follow SSH traffic.-Y "<filter>", so that you don't have to wade through all network traffic to find the bits you are interested in and as soon as Wireshark starts you'll be looking at the right data as packets appear. For example, if you are working on webRTC, then you are probably interested in STUN and DTLS messages, so your filter may be "stun or dtls;" Wireshark display filters could be further tuned, and you can even filter on IP address and port number to reduce the amount of data you need to inspect.
References
sshd: https://linux.die.net/man/8/dropbear- passing environment variables over SSH: https://superuser.com/questions/48783/how-can-i-pass-an-environment-variable-through-an-ssh-command
- display filters: https://wiki.wireshark.org/DisplayFilters

